Welcome to another Hack the Box Walkthrough. Today, we are going to show you how I pwned the Runner machine on Hack The Box. Hack The Box is a cybersecurity platform that helps you bridge knowledge gaps and prepares you for cyber security jobs.
You can also test and grow your penetration testing skills, from gathering information to reporting. If you are new to this blog, please do not forget to like, comment and subscribe to my YouTube channel and follow me on LinkedIn for more updates.About the Machine
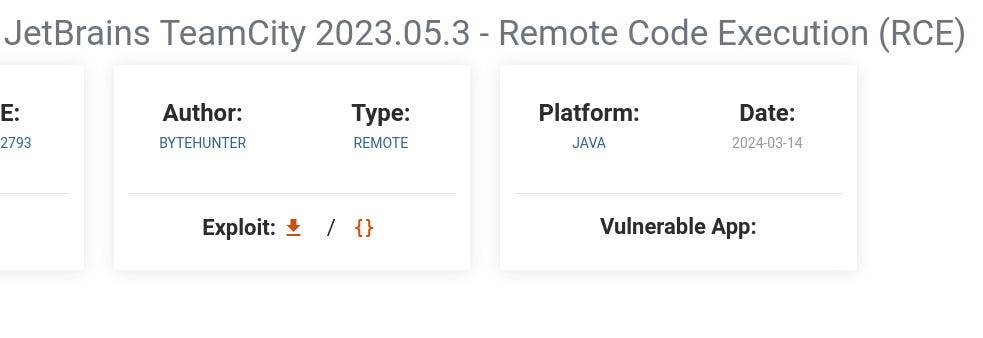
Runner is a medium difficulty Linux box that contains a vulnerability CVE-2023-42793 in TeamCity. This vulnerability allows users to bypass authentication and extract an API token, which can be used to enable debug features for executing system commands. By gaining access to a TeamCity docker container and compressing the HSQLDB database files, we can extract credentials for the user matthew and find an SSH key for john. After cracking the password, we can authenticate on the host filesystem. Upon inspecting the /etc/hosts file, we discover a running Portainer instance. Using `matthews` credentials, we access the subdomain externally. While authenticated, we find that we can create images, but our privileges are limited. After checking the version of runc on the host, we exploit a vulnerability CVE-2024-21626 through the image build function of Portainer, which allows us to create a SUID bash file on the host.
The first step in solving this machine was connecting my Kali Linux terminal to Hack the Box server. I logged into my Hack the Box account inside my Firefox browser on my Kali Linux. After I have successfully logged in, I downloaded the OpenVPN file and rename it to lab.ovpn and copy it into the “Runner HTB” folder on my desktop. Then, I launched my terminal and run the following command to connect my Kali Linux to the Hack the Box server:
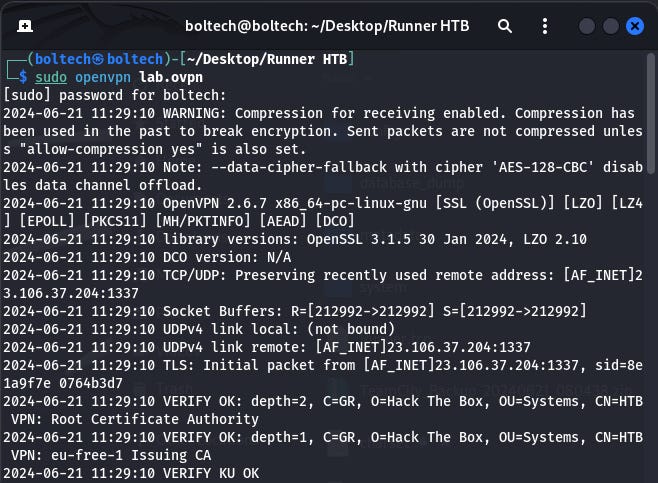
This will establish a connection between my Kali Linux and hack the box platform openvpn. Once this connection has been successfully setup, I started the Runner machine, and I was assigned an IP address of 10.10.11.13.
The second step in solving this machine is to perform enumeration using nmap. I am going to launch my terminal on my Kali Linux and type the following commands. There are several ways to scan for open ports using nmap. We can use any of the commands to find the ports that are opened by connecting to the Runner machine IP address.
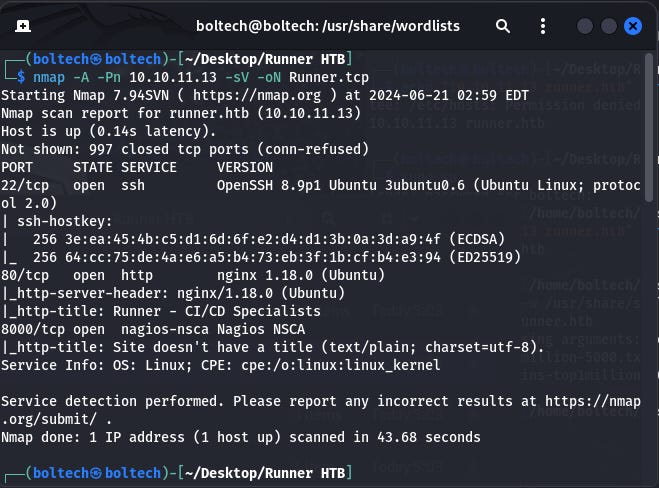
I found three open ports after scanning with nmap. The ports are 22/tcp, 80/tcp and 8000/tcp.
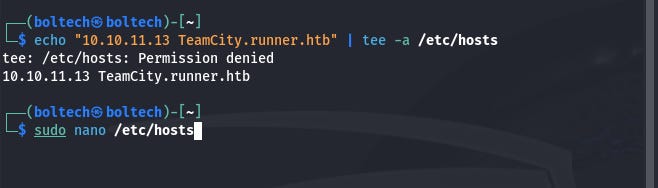
The next step is adding runner.htb to the /etc/hosts folder. There are two ways you can go about this. One is using:
If this doesn’t work, you can add sudo in front of the echo command to become something like this:
Afterwards I performed a directory scan using the following command:
Unfortunately, I couldn’t find anything useful in the directories. So, I tried virtual host blasting by running the following command:
Also, I couldn’t find anything using virtual host blasting. Next, I tried a directory search to find valuable information that could be useful in hacking the machine, so I ran the following commands to search for other directories on the Runner machine.
Also, I couldn’t find any useful information or directories that could help me to solve this machine. This was getting quite interesting!!!. The next method was using Gobuster to uncover hidden directories and files on the target machine.
I downloaded the subdomains-top1million-5000.txt file from GitHub, then moved it into the directory in the following manner usr > share > seclists > discovery > DNS (Note: You must create this directories yourself or point directly to the part where you've downloaded it) and run it together with the gobuster tool by also specifying the URL of the target machine/IP address.
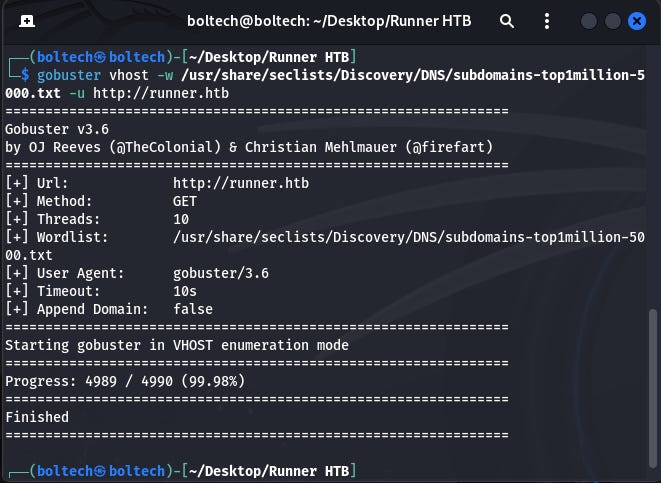
If this shows an error that the wordlist top1million-5000.txt file cannot be found, search for seclists/Discovery/DNS/subdomains-top1million-5000.txt on GitHub and download it. Tip: If it returns an error that the path does not exist, right click on the txt file, copy and paste it directly in your terminal. This will point directly to the location of the file on your machine.
Once the file has been downloaded, I navigated to /usr/share directory and create the following directory in this order seclists > Discovery > DNS and move the subdomains-top1million-5000.txt file into the DNS directory.
After this has been completed, I opened a new terminal without navigating into any directory and created a customize word list using cewl command and then used gobuster to find other url that are present on the host machine.
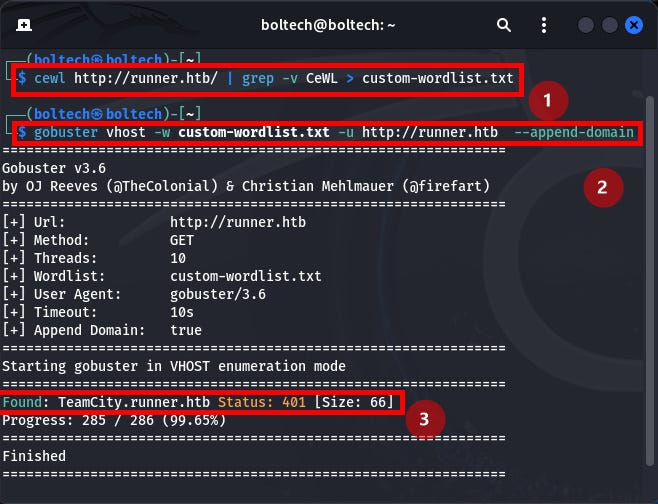
I found teamcity.runner.htb URL and I added this into my /etc/hosts file by running the following command in the terminal:
Alternatively, you can add this to the /etc/host file as a super user by running the following command:
or
(This opened the GNU command line interface and I added the IP address and the domain name I want it to redirect to)
Next, I opened the browser on my Kali Linux machine and visited http://teamcity.runner.htb/login.html
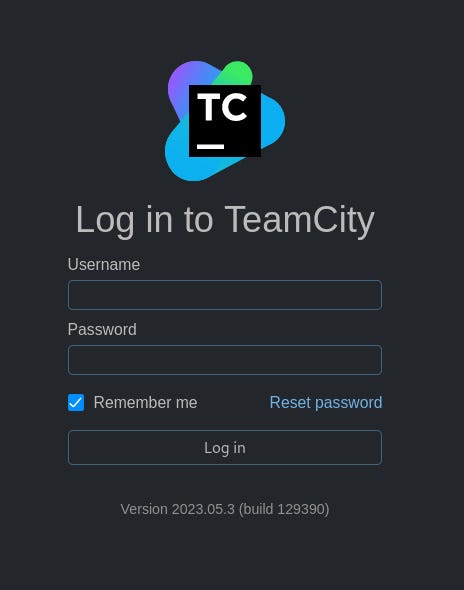
A login screen with a username and password text input field appeared. I noticed that below the login button, there’s a build version number 2023.05.3 (build 129390) of the Teamcity website. I tried to find the exploit for this version to see if I can bypass the login screen or a common/default username and password.
Luckily, I found a Remote Code Execution for this version on exploit database website and I downloaded the file.
This downloaded a python file (51884.py) and I copied this into my “Runner HTB” folder. After copying the file, I launched my terminal and ran the python file using the following command:
This displayed a username and password I can use to sign in into Teamcity website.
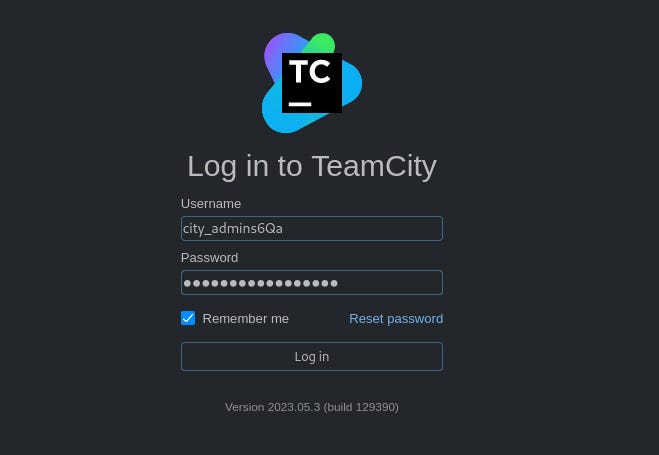
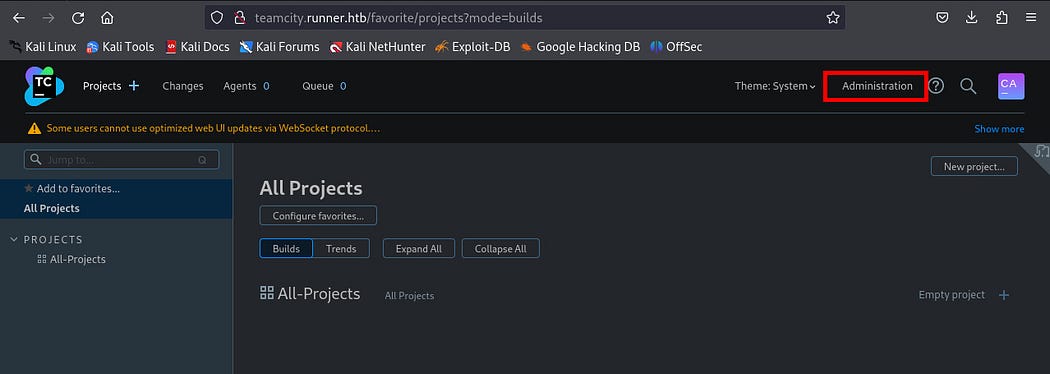
After I have successfully logged in, I navigated to “Administrator” at the upper right corner of the screen.
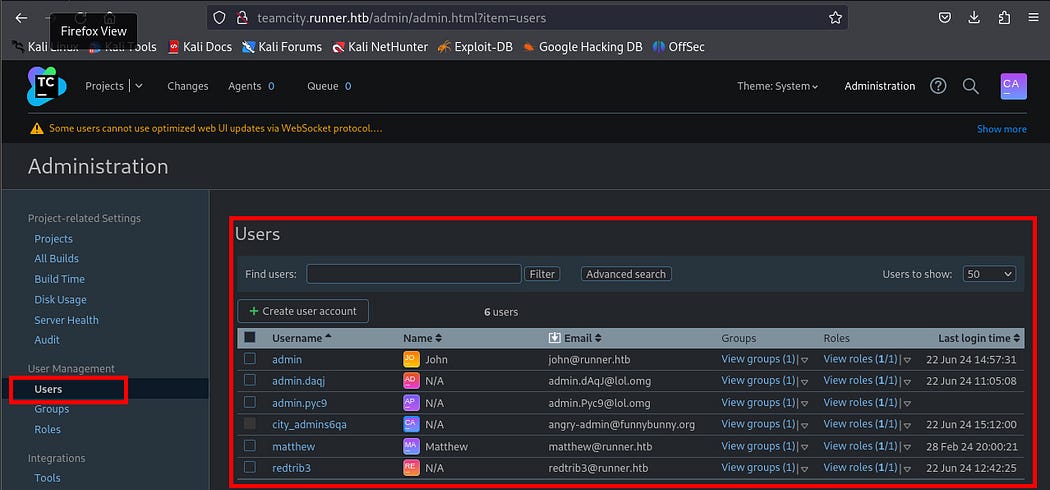
I navigated to “User” tabs and there I found multiple users, their email addresses and the roles associated with each one of them.
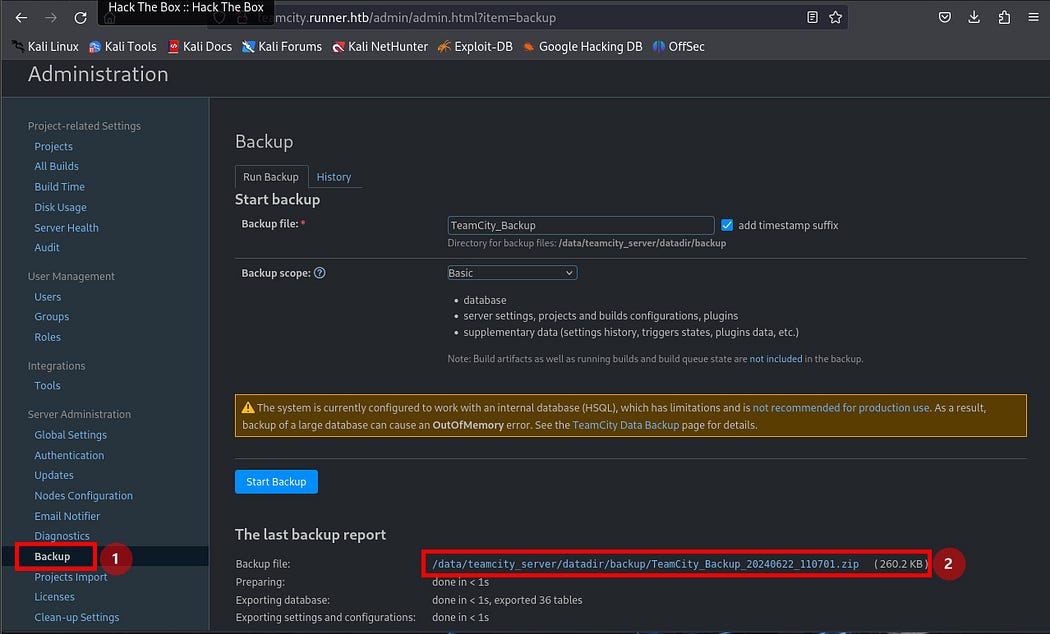
Next, I clicked the “backup” tab. I will hover over the blue link of “Backup file” and click on it. This will download the backup zip file.
I navigated to the folder where the file has been download and unzip it. In my own case, I moved the file into the “Runner HTB” folder on my desktop by running the following command while I am still in the folder “Runner HTB”
After moving the teamcity_backup zip folder into the Runner HTB runner, I unzipped the file using the following command:
Next, I performed enumeration using the following commands. While enumerating, I found out that there is an id_rsa file in the backup folder.
Alternatively, you can find the id_rsa file in
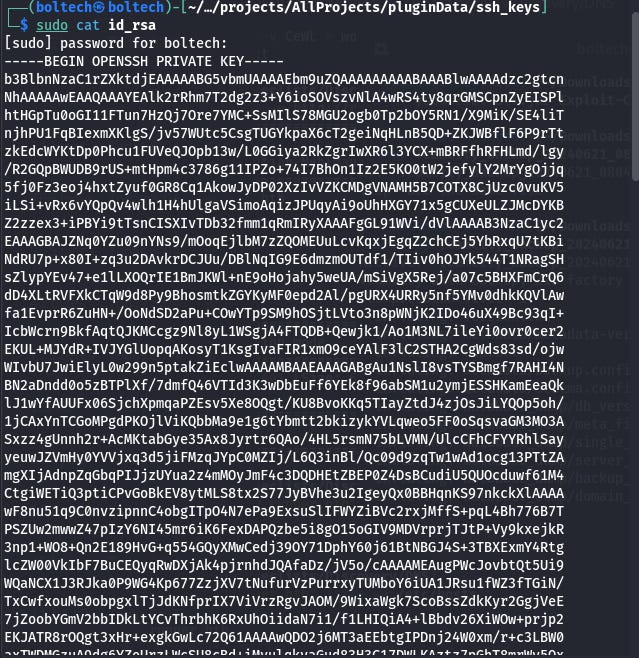
I navigated into the directory above and open the id_rsa file using the following command:
This opened the file id_rsa and it will displayed the content of the file. In the file, I found the OPENSSH Private Key and other hash values in the file.
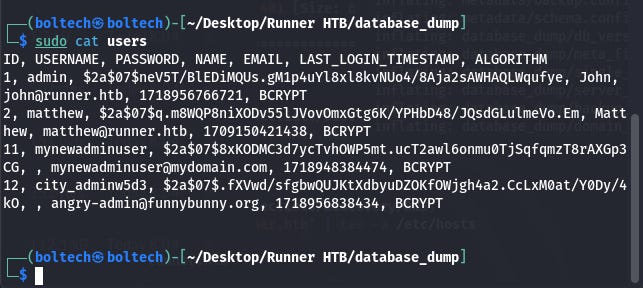
Afterwards, I navigated to the folder titled database_dump. Once I am inside the folder, I tried to find the file called users and open it using the following commands:
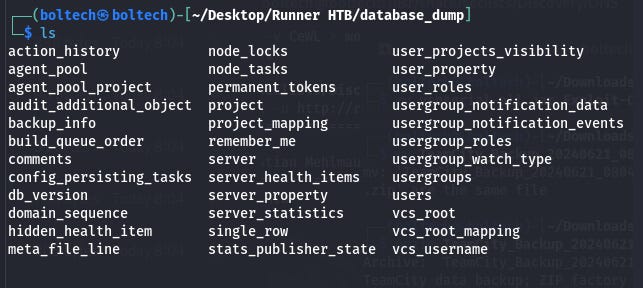
When I opened the file “users”, I found different usernames and passwords including last login timestamp, id, name and email address of each of the users.
Next, I tried to crack the id_rsa hash by using john the ripper hash crack command. To do this, I changed to super user by running this command in the terminal:
This changed the shell from boltech@kali to root@kali and I ran the following commands in the terminal:
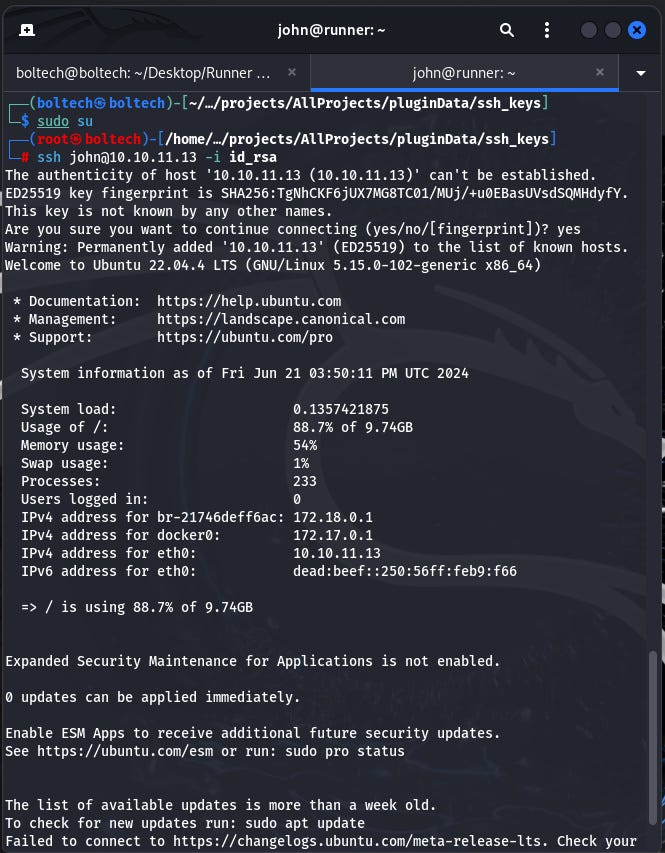
Obtaining the user flag
After I obtained john@runner shell, I ran the ls command to list the files in the directory (shell) and I got the user.txt file which I read using the following command:

Here is the result of my readings. I got the user flag (hurry!!!)
Next, I looked for a way to obtain root flag. The first thing I did was to check the open ports by running the following command:
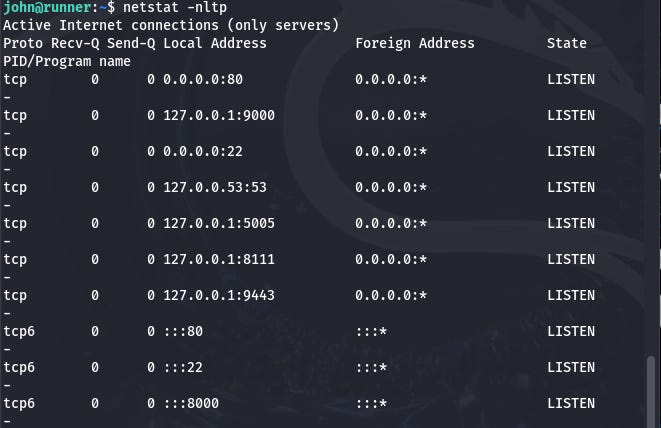
There seems to be something interesting at port 9000. So I forwarded it to myself by running the following command:
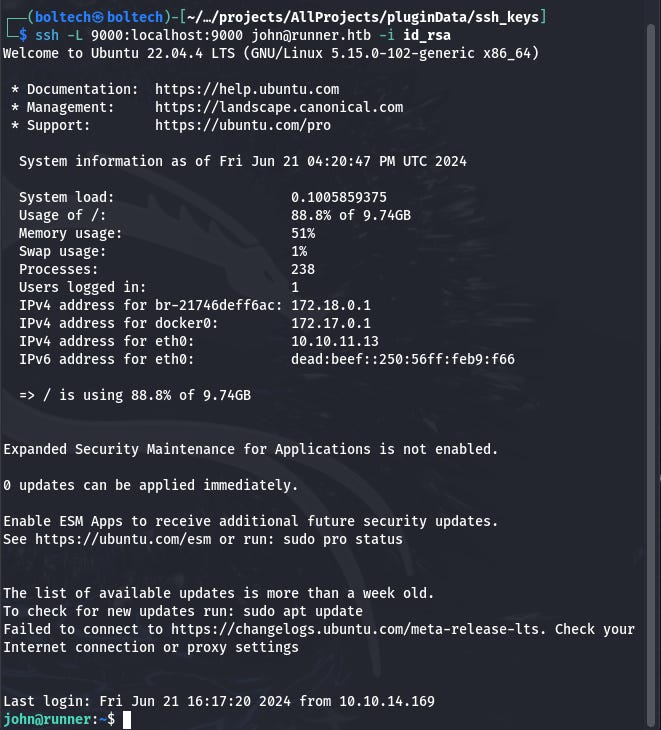
Next, I tried to crack the hash of either john or matthew by using john the ripper.
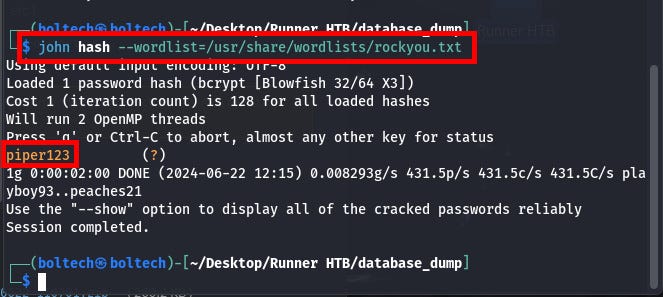
Firstly, I created a hash file inside the “database_dump” folder and I ran the following commands:
From the previous screen (image), you can see that I got piper123 as the password from the hash crack for user “Matthew”.
I performed privilege escalation. After some enumeration, I found some locally running ports. Next, I navigated to john root shell and ran the following command:

After running the command, I found some local ssh port forwarding for all open ports. The next thing I did was running the following commands:
Afterwards, I navigated to portainer.io website by visiting http://127.0.0.1:9000/. This launched portainer website and a login screen is going to pop up. Portainer is a container management software that is use to deploy, troubleshoot, and secure applications across cloud, datacenter, and Industrial IoT use cases.
Now I used matthew’s login credentials to access the portainer website. You can recall that I logged into teamcity.runner.htb where I found different users, email addresses and password credentials.
Firstly, I needed to crack the hash to find the password of the username (john and matthew). The login credentials for portainer is:
These credentials allowed me to sign in, and you can see that I am able to login into the account (from the screenshot below.)
I am on portainer.io platform, I clicked on the docker section located in the environment. Next, I navigated to “images” tab on the left hand side.
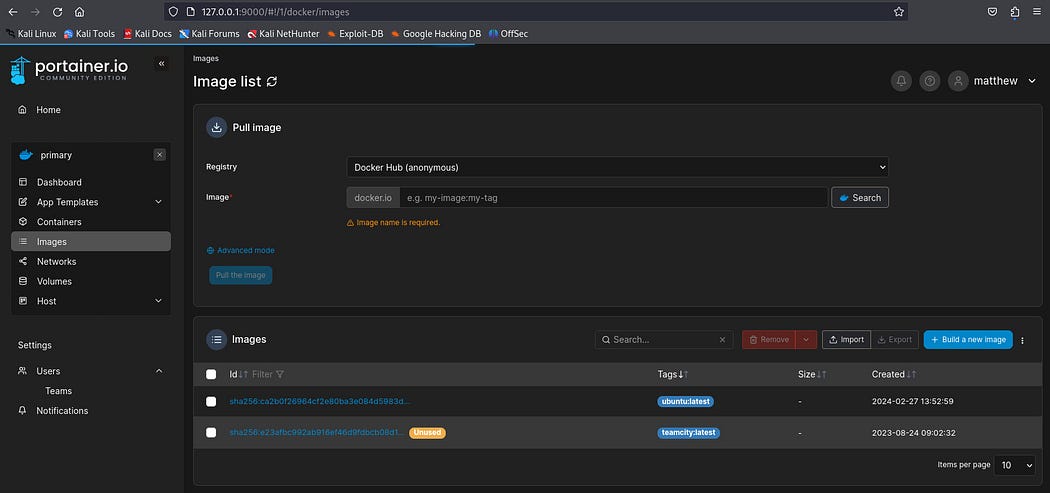
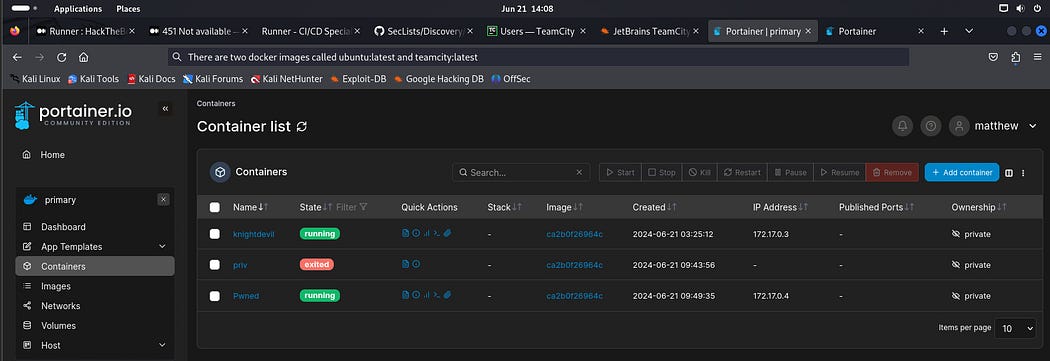
There are two docker images called ubuntu:latest and teamcity:latest
Next, I navigated into the container control panel by clicking on “container” and I clicked on “Add container” tab on the left hand side.
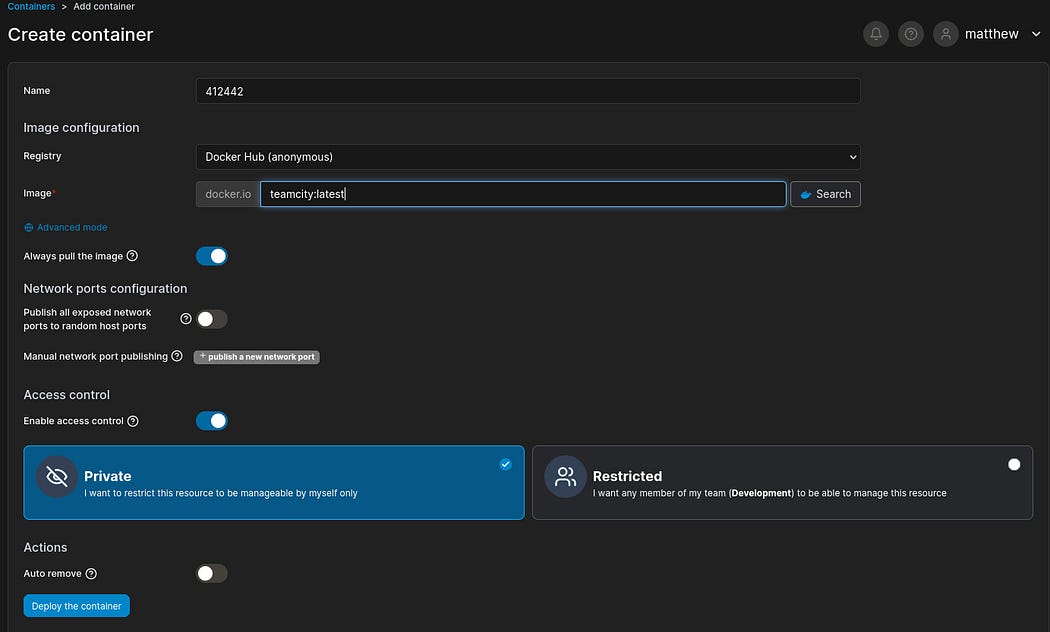
I set the following values: For the new container, I set the name to “412442”, image to “teamcity:latest” and I made sure the following options are true for “Always pull the image” & “Enable access control.” In the “advanced container settings”, I set the working dir to take the value:
Once I am done setting this, I clicked on the button “Deploy the container” to deploy the container.
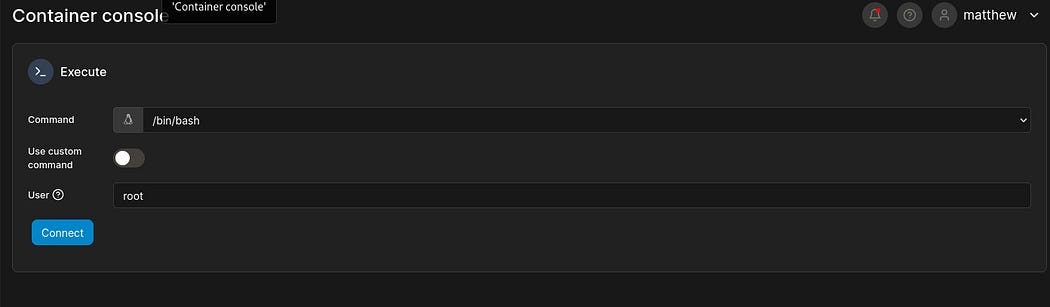
Next, I navigated to the container named “412422” and click on “console” this launched the container console and I typed “root” in the user text field and clicked on connect to launch the terminal.
Once my terminal has been successfully launched, I read my root flag by running the following commands:
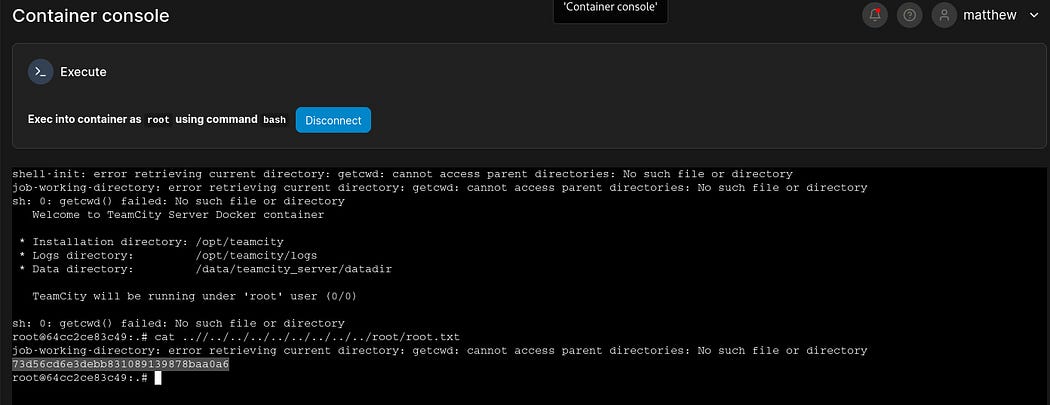
Hurry!!! I got our root flag
Congratulations if you made it this far. If you enjoy reading my writeups, kindly subscribe to my channel and follow me on my social media handles:
YouTube channel: https://m.youtube.com/@BoltechTechnologies1
LinkedIn https://www.linkedin.com/in/isiaq-ibrahim-468588156/
Twitter at https://x.com/BoltechNG
Follow me on Medium: https://medium.com/@ibrahimbolaji50.ib
This walkthrough was first published on Medium on June 25 2024. The walkthrough had 23 views and 9 reads on Medium and 489 views on YouTube.


















0 Comments